The Silent Collection – Part 1: The Dossier Takes Shape
Not everyone who takes an interest in you intends to help.
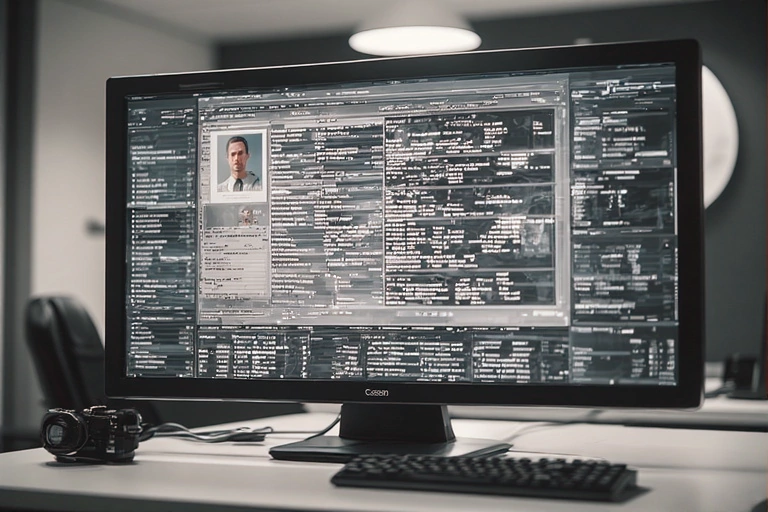
What others truly know about a person often becomes visible only when one draws too close to a sun. It does not begin with the scandal, but with the unremarkable note. A name, a marginal remark, a photograph in the background – archived. An access to a device that leaves no trace. Sometimes automated, sometimes carried out with the patience of a craft that spans months or years.
This is not indiscriminate mass surveillance. It is the deliberate compilation of personal dossiers. The subjects are those who may one day stand within a decision‑making process – in business, politics, administration, media. Those who become interesting only when they act in ways not hoped for. The selection is not a matter of whim. It follows the logic of strategic preparation: whoever seeks to secure options, secures leverage.
It is a silent process. No knock at the door, no alert on the screen. The data remain unused – for now. In an archive that now protects them more effectively than their owner ever did. On call, ready for the day of disclosure: when loyalties cool, alliances fracture, or careers move onto a collision course. Only when one stands in the way does the stored information unfold with cold brutality.
Often the strike is precise and irrevocable: a targeted leak to the press, the release of a compromising chat record, a photograph in the most unfavourable context. For the subject it feels like lightning from a clear sky – a sudden fracture in the familiar world that calls into question all that seemed secure moments before. For the collector, it is merely the triggering of a long‑prepared chain.
At times it begins not with a public blow, but with targeted, quiet pressure: a document that should never have surfaced. Information that only you should have known, now in foreign hands. An untraceable call – brief, factual, yet unmistakable. The message: one could act. The unspoken expectation: resignation “for personal reasons”, withdrawal of a candidacy, abandonment of an undertaking.
The technology behind it is both banal and refined: metadata, location logs, surveillance during sensitive meetings in places you did not choose, old emails in forgotten mailboxes. Device backups stored in cloud systems, on servers that should never have been targets. OSINT methods that can derive an almost seamless profile from open sources. And how often has one, under time pressure, overruled instinct when it urged caution. For the one who knows how, the collection is no art – the art lies in persistence and in the choice of the moment.
Data concerning conversations with psychologists are particularly coveted by collectors – and therefore demand special protective measures, both technical and behavioural. It is no longer sufficient to guard only against accidental indiscretions and to operate in compliance with data protection regulations, when targeted attacks are among the realistic scenarios. Pseudonymous consultation is a good beginning, yet without a coordinated security concept it is not enough. A collector will seek to exploit precisely this pseudonymity as an attack vector – not technically, but through behaviour, through social engineering, to reach the “crown jewels”. Without firmly implemented and binding safeguards for the pseudonymous identity, invisibility quickly becomes a trap.
To feel secure merely because “nothing has happened” so far, even without special precautions, serves the collector – not you. The same applies to the habit of hastily placing those with a higher demand for discretion in the vicinity of eccentric paranoia.
Those who think in this way open doors without intending to – and it is precisely here that consistent discretion makes the difference. In such cases it is more than a theoretical ideal – it is indispensable. For what cannot be reconnoitred cannot be positioned against you. Every poorly protected data set is a potential round; whether and when it will be chambered is decided by others.
Publications The Conversation Contact Main Page
Publication Details
- Author: Meisters, K.-H.
- APA Citation: Meisters, K.-H. (2025, September 23). The Silent Collection – Part 1: The Dossier Takes Shape. Retrieved from https://k-meisters.de/en/texte/text-039.html
- First published: September 23, 2025
- Last modified on: September 23, 2025
- Licence & Rights: © 2025 Meisters, K.-H. – All rights reserved
- Contact for licensing inquiries: licensing@k-meisters.de
Impressum (German) | Impressum (English translation) | Datenschutzerklärung (Privacy Policy, German) | Privacy Policy (English translation) | Contact
Important Notice: I, Karl‑Heinz Meisters, am a graduate psychologist. My work is limited to conversations intended for personal development and clarification. I am not a physician, alternative practitioner, or psychotherapist, and I do not practise medicine as defined by applicable health‑care laws. I do not provide diagnoses, treat or alleviate illnesses, or offer medical services. My work does not include legal advice and is neither to be understood in the legal sense nor as a legal service.
K-meisters.de is my sole online presence. No additional digital profiles or social‑media accounts exist or are planned.
Talks and formats are offered exclusively in closed, non‑public circles.
Definition of “Private Guest”: The term “private guest” is used here in a non‑legal sense, referring to individuals who engage in preliminary conversations without any contractual relationship.
Definition of “Engagement”: Within the scope of my psychological consulting, the term “engagement” refers to a formal agreement to work together. This applies equally to related expressions such as “advisory engagement” or “engaged client.” My services do not include legal advice and are not to be interpreted as a legal service.
Image Credit: The images on this page were created with the assistance of artificial intelligence (Stable Diffusion via Perchance.org – https://perchance.org/ai-text-to-image-generator). They are subject to the Stability AI Community License – https://stability.ai/license – and are used in accordance with its terms. The images are for illustrative purposes only and do not depict any real person, brand, or protected work. Exceptions, where applicable, are noted below this paragraph.
© 2025 Karl‑Heinz Meisters – All rights reserved. All content, text, and concepts are protected by copyright. The communication concept presented here has been published by me as a structured work and is subject to copyright law. Any use, reproduction, or exploitation is permitted only with my prior written consent.